Researchers Prove Rabbit AI Breach By Sending Email to Us as Admin
Excerpt
The researchers claim they could see “all Rabbit R1 responses ever given.”
Join the newsletter to get the latest updates.
Members of a community focused on jailbreaking and reverse engineering the Rabbit R1 AI assistant device say that Rabbit left critical API keys hardcoded and exposed in its code, which would have allowed them to see and download “all r1 responses ever given.” The API access would have allowed a hacker to use various services, including text-to-speech services and email sending services, as if they were the company. To verify their access, the researchers sent 404 Media emails from internal admin email addresses used by the Rabbit device and the Rabbit team.
The disclosure, which was made on the group’s website and in its Discord Tuesday, is the latest in a comedy of errors for the device, which, under the hood is essentially just an Android app that runs requests through a series of off-the-shelf APIs like ElevenLabs, which is a text-to-speech AI product. The device’s poor design has been the subject of many articles, investigations, and YouTube videos.
The exposed API keys were discovered by a group called Rabbitude, a community of hackers and developers who have been reverse engineering the Rabbit to explain how it works, find security problems, jailbreak the devices, and add additional features. “We reverse, hack, and experiment with the r1 and report our findings publicly,” Rabbitude explains on its website. “Rabbitude is built by the community along with some core members. overall making the r1 experience better.”
In a blog post Tuesday, Rabbitude explained that Rabbit “has known that we have had their ElevenLabs API key for a month, but they have taken no action to rotate the API keys.”
“On may 16, 2024, the rabbitude team gained access to the rabbit codebase and found several critical hardcoded api keys in its code. these keys allow anyone to:
- read every response every r1 has ever given, including ones containing personal information
- brick all r1s
- alter the responses of all r1s
- replace every r1’s voice”
The group stated that the exposed API keys were for ElevenLabs, Microsoft’s Azure, Yelp, and Google Maps. The group also told 404 Media separately that it had the API key for SendGrid, Rabbit’s email provider. Rabbitude wrote a second blog post about the SendGrid exposure Wednesday: “it provides access to a complete history of emails sent on the rabbit.tech domain and its subdomains. this includes company data, like internal spreadsheets and communications, as well as media and security responses.”
API keys for artificial intelligence services are highly sensitive. They are essentially digital keys that allow a person or company to integrate that service into other products, in this case, the Rabbit R1. That specific key then allows the AI services company to track usage of that account and charge the person or company using it. For that reason, these are incredibly sensitive and should not normally be hard coded into source code. ElevenLabs tells its users “If someone gains access to your API key he can use your account as he could if he knew your password.”
“The normal approach to secrets management would be: rather than hard coding secret keys / values into the code itself, instead keys should be ‘injected’ in some form at runtime,” Emily, a researcher with the group, told 404 Media. “The interesting part of all of this is that Rabbit deploy all of their code in containers, managed by kubernetes which natively supports managing both environment variable and file based secret and config value injection at runtime for you, so using these methods should have been an absolute no brainer.”
In a statement, Rabbit said “Today we were made aware of an alleged data breach. Our security team immediately began investigating it. As of right now, we are not aware of any customer data being leaked or any compromise to our systems. If we learn of any other relevant information, we will provide an update once we have more details.”
Rabbitude said that Rabbit rotated the API key for ElevenLabs Tuesday after their blog post was published. 404 Media could not independently confirm this, but Rabbit users on the official Discord stated that their devices temporarily stopped working for a few minutes Tuesday, which would be consistent with ElevenLabs being unavailable.
A screenshot from the Rabbit launch event showing that rabbit@r1.rabbit.tech is an email address used by the company
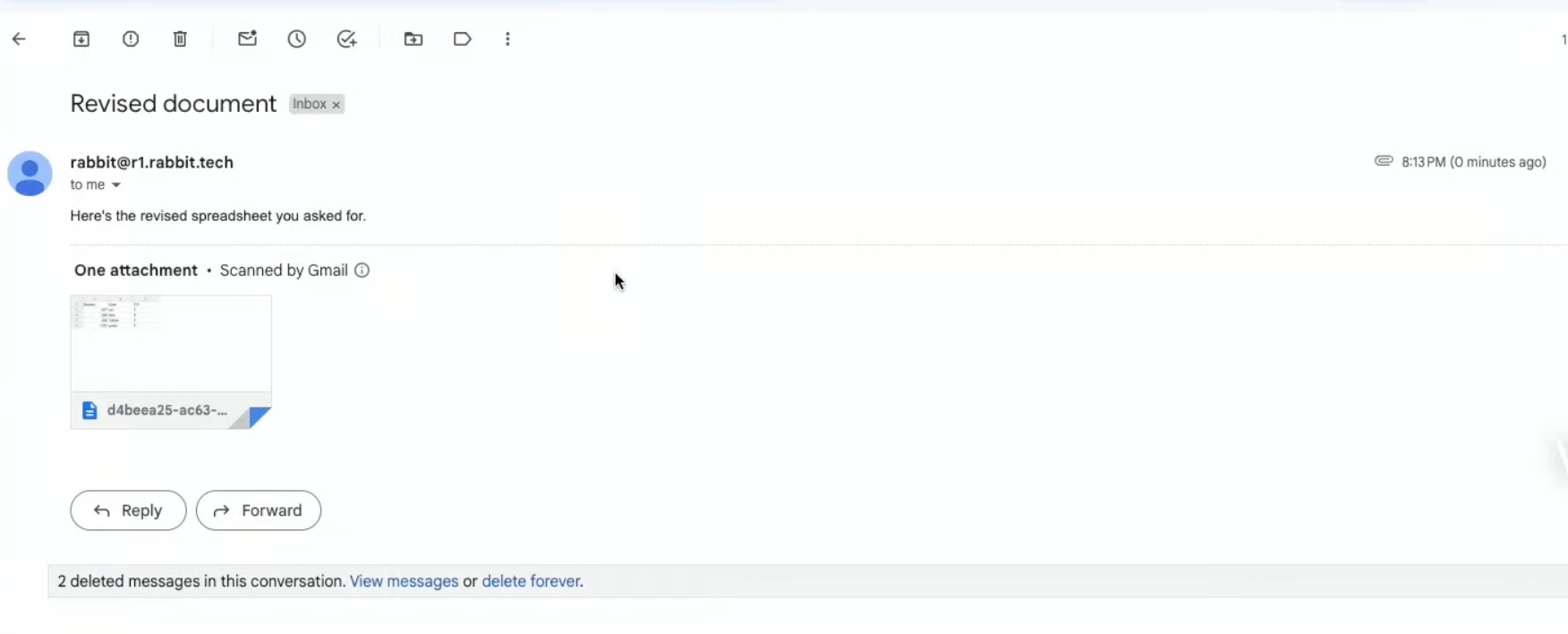
An email sent to 404 Media by the researchers
Another email sent to 404 Media by the researchers, using an internal Rabbit email address.
I then followed up with Rabbit to ask if any API keys were exposed or rotated, and Rabbit said “Since our team is currently investigating, we do not have any other details to share at this time.”
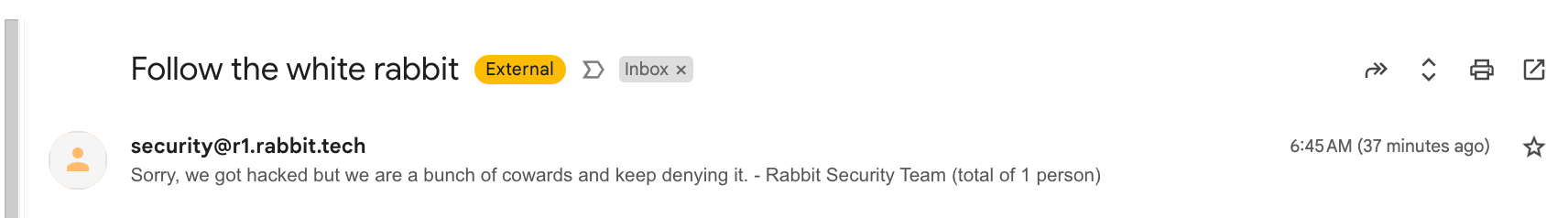
I then asked one of the researchers, named Eva, what she thought about Rabbit’s statement. She then sent me an email from an internal Rabbit email address that was previously used to send an email in the device’s launch Keynote, rabbit@r1.rabbit.tech: “Hi there, Jason.” She then sent two more emails from “security@r1.rabbit.tech.”
“Sorry, we got hacked but we are a bunch of cowards and keep denying it. - Rabbit Security Team (total of 1 person),” the researchers said to me and several other journalists in an email sent from the internal Rabbit security email address.
Eva said that the team was able to send these emails because they still had access to the SendGrid API key. Eva previously exposed flaws in Chattr, an AI hiring chatbot used by fast food companies.
“I think [Rabbit’s statement] is untruthful, to be honest, because while yes we didn’t steal user data, so the statement that no ‘customer data being leaked’ is, by its most pedantic definition, true, the compromise of us having access to the key happened and had we been malicious we very much could have accessed things we shouldn’t have been able to,” Emily said. “The fact that we were responsible in not doing anything with it in no way negates that they were irresponsible in both how they stored their keys in the codebase in the first place and how they (didn’t) react to the knowledge that we had had access to the codebase in the second place.”
In a video last month, the YouTuber Coffeezilla, who has been doing investigations into Rabbit, said “I also have reviewed parts of the Rabbit source code, and I also have serious data privacy concerns. There are things in this codebase, and I can’t share it for reasons that will become obvious. There are things that malicious actors could use to get any access to replies Rabbit has ever given.” Emily said in the Rabbitude Discord that “we were working with Coffeezilla at the time—he and our team had access to the code in question as part of our investigation. The public disclosure today is what he was talking about. This is real. Rabbit can dance around it all they like but it is real, and this did happen. They had a month to change the keys, and they didn’t. That’s on them.”
Several hours after this article was originally published, Rabbit created a security page on its website and posted the following statement: “On June 25, 2024, we were notified that a third-party may have had access to working API keys for multiple SaaS providers used by rabbit to provide services to our customers. Based on this notice, the rabbit security team rotated the keys to those APIs, which caused a brief downtime on the devices. Our team is continuing our investigation. As of today, we have not found there to be any compromise of our critical systems or of the safety of customer data.”
Update: This piece has been updated to add Rabbitude’s writeup of the SendGrid API exposure. It has also been updated to add that Rabbit acknowledged it has rotated exposed API keys.
About the author
Jason is a cofounder of 404 Media. He was previously the editor-in-chief of Motherboard. He loves the Freedom of Information Act and surfing.